Torzon Security Features
Military-grade protection with post-quantum cryptography, multisig escrow, and comprehensive anti-phishing measures to keep your transactions and identity safe.
Torzon Market Security Architecture Overview
Security is the cornerstone of any successful darknet marketplace, and Torzon Market has built its entire infrastructure around protecting users from every conceivable threat. Unlike traditional e-commerce platforms that rely on centralized security measures, Torzon implements a multi-layered defense system that addresses threats from hackers, law enforcement, exit scams, and phishing attacks simultaneously. This comprehensive approach has established Torzon as one of the most secure marketplaces in the darknet ecosystem.
The Torzon security model operates on the principle of defense in depth. Rather than relying on a single security measure, the platform combines multiple overlapping protections that work together to create an impenetrable barrier against attackers. Even if one layer is compromised, the remaining layers continue to protect users and their funds. This approach has proven remarkably effective, with Torzon maintaining a perfect security record since its launch in 2022.
What truly sets Torzon apart from competitors is its forward-thinking adoption of post-quantum cryptography. While most darknet markets still rely on traditional encryption methods that could potentially be broken by quantum computers in the future, Torzon has already implemented quantum-resistant algorithms that will remain secure regardless of technological advances. This proactive approach demonstrates Torzon's commitment to long-term user protection.
Security Statistics
- Zero successful hacks since platform launch in 2022
- 100% fund recovery rate for disputed transactions
- Post-quantum encryption protecting all communications
- 2-of-3 multisig escrow preventing exit scams
- 24/7 security monitoring by dedicated team
Post-Quantum Cryptography: Future-Proof Protection
Quantum computing represents the most significant threat to current encryption standards. Traditional cryptographic algorithms like RSA and ECC rely on mathematical problems that are extremely difficult for classical computers to solve but could be cracked by sufficiently powerful quantum computers. Torzon Market recognized this emerging threat early and became one of the first darknet platforms to implement post-quantum cryptographic algorithms.
Understanding the Quantum Threat
Classical encryption works by creating mathematical puzzles that would take conventional computers billions of years to solve through brute force. Quantum computers, however, can use algorithms like Shor's algorithm to solve these puzzles exponentially faster. A quantum computer with enough qubits could theoretically break RSA-2048 encryption in mere hours, exposing all data protected by traditional cryptography.
While large-scale quantum computers capable of breaking current encryption don't exist yet, security experts predict they could emerge within the next decade. Data encrypted today using traditional methods could be recorded by adversaries and decrypted later when quantum computers become available. This "harvest now, decrypt later" attack makes it essential to implement quantum-resistant encryption today, especially for sensitive darknet marketplace communications.
Torzon's Quantum-Resistant Implementation
Torzon implements lattice-based cryptography, one of the most promising post-quantum cryptographic approaches. Lattice problems are believed to be resistant to both classical and quantum computing attacks. The platform uses a combination of CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures, both of which are NIST-approved post-quantum algorithms.
All sensitive communications on Torzon are protected by these quantum-resistant algorithms, including:
- Buyer-vendor encrypted messages
- Order details and shipping addresses
- Account credentials and session tokens
- Transaction signatures and escrow communications
- PGP key exchanges and verification
What This Means for Users
Your communications and transaction data on Torzon are protected not just against current threats, but against future quantum computer attacks. Even if an adversary records your encrypted messages today, they won't be able to decrypt them when quantum computers become available. This forward-thinking protection is unique among darknet marketplaces.
2-of-3 Multisig Escrow: Eliminating Exit Scam Risk
Exit scams have plagued the darknet marketplace ecosystem since its inception. From the original Silk Road's seizure to notorious exit scams by markets like Evolution and Empire, users have lost millions of dollars when marketplace administrators absconded with escrowed funds. Torzon's implementation of 2-of-3 multisignature escrow fundamentally eliminates this risk by ensuring no single party can unilaterally access escrowed funds.
How Traditional Escrow Fails
In traditional marketplace escrow, the platform holds buyer funds until the transaction completes. This creates a central point of failure where the marketplace administrators have complete control over user funds. If administrators decide to exit scam or are compromised by hackers, all escrowed funds can be stolen instantly. Users have no recourse and no way to recover their cryptocurrency.
The Multisig Solution
Multisignature (multisig) technology changes this dynamic entirely. Instead of sending funds to a wallet controlled by the marketplace, buyers send Bitcoin to a special address that requires multiple signatures to spend. Torzon uses a 2-of-3 configuration, meaning the wallet requires any two of three possible signatures: the buyer, the vendor, or Torzon market.
Transaction Flow with Multisig
- Order Placement: When a buyer places an order, a unique multisig address is generated with keys held by the buyer, vendor, and Torzon.
- Funding: The buyer sends the required Bitcoin amount to this multisig address. The funds are now locked and require 2 signatures to move.
- Normal Completion: If the order is delivered successfully, the buyer and vendor both sign a transaction releasing funds to the vendor.
- Dispute Resolution: If there's a problem, Torzon can sign with either the buyer or vendor to release funds to the appropriate party.
- Auto-Finalize: After a specified period without disputes, the system automatically processes the release with buyer and market signatures.
Why Exit Scams Are Impossible
The critical security benefit of 2-of-3 multisig is that Torzon administrators can never steal user funds on their own. Even if every Torzon administrator decided to exit scam, they only hold one of the three required keys. They would need either the buyer's or vendor's signature to move any funds, which honest users would never provide for illegitimate transactions.
This mathematical guarantee makes Torzon fundamentally different from traditional escrow marketplaces. Your funds are protected by cryptographic certainty, not by trusting marketplace administrators. Even in a worst-case scenario where Torzon is compromised or goes offline, users retain control of their funds through their private keys.
Important: Secure Your Keys
Multisig protection requires you to properly manage your private keys. Never share your multisig signing key with anyone, and store backups securely. If you lose your key, you may need to rely on Torzon support to help resolve transactions, reducing your control over fund disputes.
Comprehensive Anti-Phishing Protection
Phishing represents one of the most dangerous threats facing darknet marketplace users. Malicious actors create convincing fake versions of marketplace login pages, tricking users into entering their credentials on phishing sites. These attacks have resulted in millions of dollars in stolen funds and compromised accounts across the darknet ecosystem. Torzon implements multiple overlapping protections to ensure users can always verify they're on the authentic site.
Personal Anti-Phishing Phrase
During account registration, every Torzon user creates a unique personal anti-phishing phrase. This phrase is displayed prominently on the login page after entering your username, but before you enter your password. Since only the real Torzon servers know your personal phrase, phishing sites cannot display it correctly.
The anti-phishing phrase system works because the phrase is stored server-side and only revealed after username verification. Even if a phishing site knows your username, they cannot retrieve your personal phrase from Torzon's servers. If you ever reach a login page that doesn't show your correct phrase, you know immediately that you're on a phishing site.
Visual Security Indicators
Beyond the personal phrase, Torzon implements multiple visual security indicators:
- Customizable security image: Choose a personal image displayed on your dashboard
- Account-specific color scheme: Subtle color variations tied to your account
- Last login timestamp: Shows when and from where you last accessed your account
- Active session display: View all currently active sessions
Link Verification Best Practices
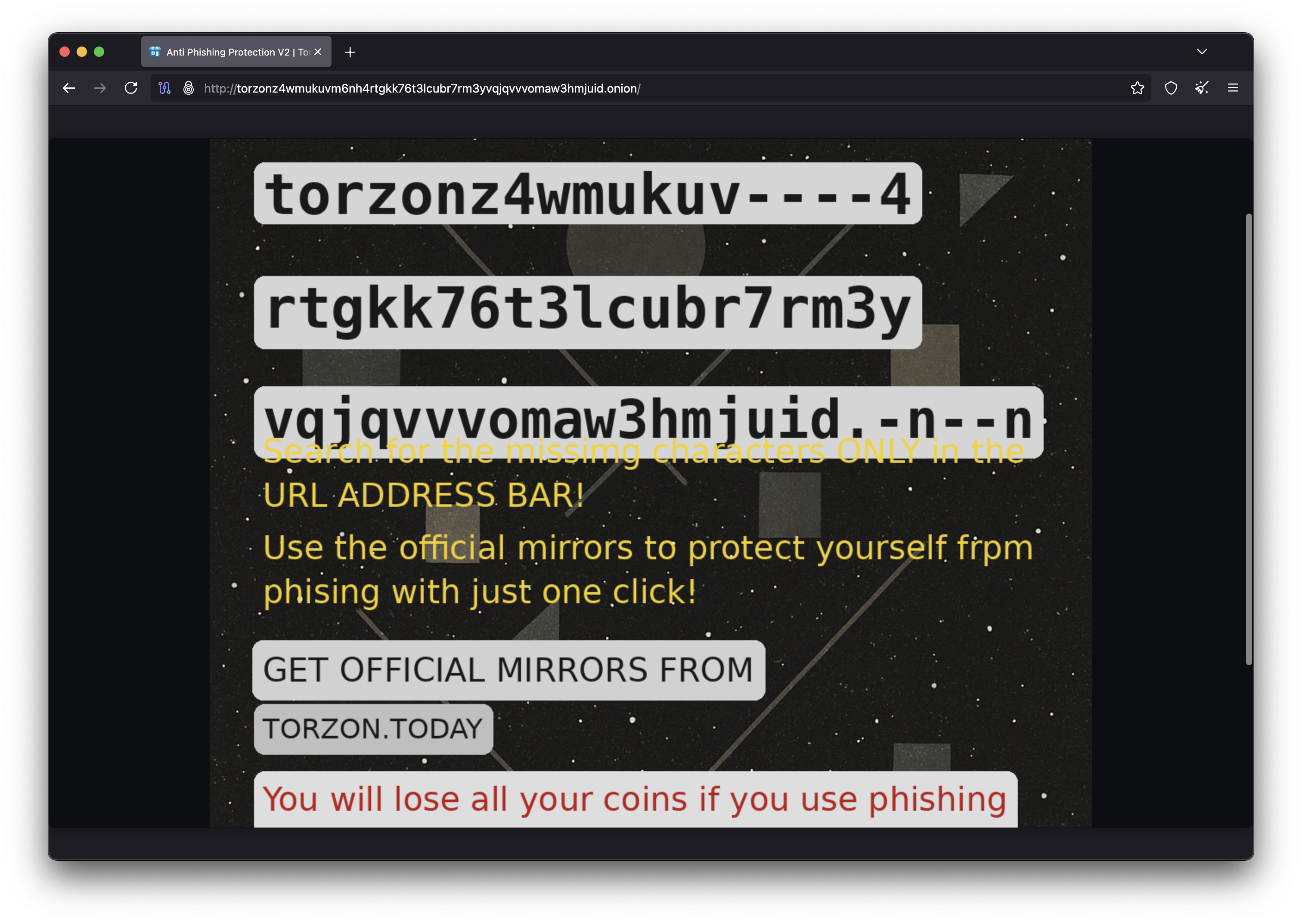
While Torzon's anti-phishing measures are robust, users should also follow these practices to avoid phishing:
- Only use links from verified sources like our official mirrors page
- Bookmark the correct .onion address and always use your bookmark
- Never click Torzon links from forums, social media, or search engines
- Always verify your anti-phishing phrase before entering your password
- Check that the .onion address matches character-for-character
- Be suspicious of any site claiming Torzon has "moved" to a new address
What To Do If You've Been Phished
If you accidentally entered credentials on a phishing site, immediately log into the real Torzon (verify your anti-phishing phrase!) and change your password. Enable 2FA if you haven't already, and withdraw any funds to a secure wallet. Report the phishing site URL to Torzon support to help protect other users.
Two-Factor Authentication (2FA) Options
Even the strongest password can be compromised through phishing, malware, or data breaches. Two-factor authentication adds a crucial second layer of security by requiring something you have (a physical device or key) in addition to something you know (your password). Torzon offers multiple 2FA options to accommodate different security preferences and threat models.
PGP-Based Two-Factor Authentication
PGP 2FA is the most secure option available on Torzon and is strongly recommended for all users. When enabled, the login process requires you to decrypt a challenge message using your private PGP key. Since your private key never leaves your device, this provides strong protection even if your password is compromised.
The PGP 2FA process works as follows:
- Enter your username and password as normal
- Torzon encrypts a random challenge string with your public PGP key
- You decrypt this message using your private key and PGP software
- Enter the decrypted challenge to complete login
PGP 2FA provides the strongest protection because it's based on asymmetric cryptography. The private key required for decryption never touches Torzon's servers, so there's no central database of 2FA secrets that could be compromised in a breach.
TOTP Authenticator Apps
For users who prefer convenience over maximum security, Torzon also supports Time-based One-Time Password (TOTP) authentication. This works with standard authenticator apps like Google Authenticator, Authy, or Aegis. After scanning a QR code to set up your account, you'll enter a 6-digit code that changes every 30 seconds.
While TOTP is less secure than PGP 2FA (the shared secret is stored on Torzon's servers), it's still far more secure than password-only authentication and may be more practical for mobile users or those unfamiliar with PGP software.
Security Key Support
Torzon supports hardware security keys compatible with the FIDO2/WebAuthn standard. Physical security keys like YubiKey provide excellent phishing resistance because they cryptographically verify the site you're logging into matches the site where the key was registered. Even if you're tricked into visiting a phishing site, your security key will refuse to authenticate.
2FA Comparison
| Method | Security Level | Convenience | Phishing Resistance |
|---|---|---|---|
| PGP 2FA | Highest | Low | High |
| Security Key | Very High | High | Very High |
| TOTP App | High | High | Medium |
End-to-End PGP Encryption
Pretty Good Privacy (PGP) encryption forms the backbone of secure communication on Torzon Market. All sensitive information exchanged between buyers and vendors should be encrypted with PGP, ensuring that even if Torzon's servers were compromised, attackers could not read message contents. This end-to-end encryption puts users in complete control of their communication security.
How PGP Works
PGP uses asymmetric encryption, meaning each user has two keys: a public key they share openly, and a private key they keep secret. When you want to send an encrypted message, you encrypt it with the recipient's public key. Only their private key can decrypt the message, so even the platform operators cannot read encrypted communications.
Mandatory PGP for Sensitive Data
Torzon strongly encourages (and for verified vendors, requires) the use of PGP encryption for all sensitive communications. This includes:
- Shipping addresses: Always encrypt your delivery address with the vendor's public key
- Order details: Encrypt any identifying information about your order
- Personal information: Never send unencrypted personal details
- Payment confirmations: Encrypt transaction IDs and payment details
PGP Key Verification
To prevent man-in-the-middle attacks, Torzon implements PGP key verification systems. Vendor public keys are displayed on their profile pages, and users can verify key fingerprints through multiple channels. Torzon also signs vendor keys with the market's master key, providing an additional layer of authenticity verification.
Users should always verify vendor PGP fingerprints before sending sensitive information. Compare the fingerprint shown on Torzon with fingerprints posted on vendor's external sites, signed canary messages, or previous verified communications. This verification process prevents sophisticated attacks where an adversary attempts to substitute their own public key for a vendor's.
Getting Started with PGP
New to PGP encryption? Visit our Access Guide for step-by-step instructions on setting up PGP software, generating your key pair, and encrypting your first message. While PGP may seem complex at first, it becomes second nature with practice and provides irreplaceable protection for your privacy.
Server Infrastructure Security
Beyond user-facing security features, Torzon implements comprehensive server-side protections to defend against technical attacks, law enforcement seizures, and data breaches. The platform's infrastructure is designed with security as the primary consideration, often at the expense of performance or cost efficiency.
Distributed Architecture
Torzon operates on a distributed server architecture spread across multiple jurisdictions. This design provides several security benefits:
- No single point of failure that could take down the entire platform
- Resistance to jurisdiction-specific legal pressure
- Automatic failover if individual servers are compromised
- Distributed denial-of-service (DDoS) attack resistance
Data Minimization
Torzon follows strict data minimization principles, collecting and storing only the absolute minimum information required for platform operation. Messages are automatically purged after a defined period, transaction records are anonymized after completion, and no logs of user activity are retained. This approach ensures that even a complete server compromise would yield minimal useful data to attackers.
Encryption at Rest
All data stored on Torzon servers is encrypted at rest using strong symmetric encryption. Database contents, user files, and system logs are all protected by encryption keys that are stored separately from the encrypted data. Even physical seizure of server hardware would not provide access to user data without the corresponding encryption keys.
Regular Security Audits
Torzon conducts regular security audits of its codebase and infrastructure. The platform offers a bug bounty program that rewards security researchers for responsibly disclosing vulnerabilities. This proactive approach to security has helped identify and fix potential issues before they could be exploited by malicious actors.
Security Frequently Asked Questions
Is my data safe if Torzon gets hacked?
Torzon implements multiple layers of protection that limit damage even in a worst-case breach scenario. All sensitive communications should be PGP encrypted end-to-end, meaning attackers couldn't read message contents. Passwords are hashed with strong algorithms, so they can't be recovered from database dumps. Multisig escrow means funds can't be stolen even with full server access. While no system is 100% secure, Torzon's architecture minimizes the impact of potential breaches.
Can quantum computers break Torzon's encryption?
No. Torzon has implemented post-quantum cryptographic algorithms that are resistant to both classical and quantum computer attacks. While most darknet markets still use traditional encryption that could theoretically be broken by future quantum computers, Torzon's quantum-resistant algorithms will remain secure regardless of advances in quantum computing technology.
How do I know I'm on the real Torzon?
Always verify your personal anti-phishing phrase before entering your password. This phrase is set during registration and is displayed after you enter your username. Only the real Torzon servers know your phrase, so phishing sites cannot display it correctly. Additionally, only use links from trusted sources like our verified mirrors page, and always double-check the .onion address character-by-character.
What happens to my funds if Torzon goes offline?
Thanks to 2-of-3 multisig escrow, your funds remain protected even if Torzon goes permanently offline. For active orders, you retain one of the three keys required to access escrowed funds. In an emergency, the Torzon team would release signed recovery transactions allowing users to reclaim their funds. Wallet balances not in escrow can be withdrawn at any time using your standard Bitcoin wallet.
Should I use PGP or TOTP for 2FA?
PGP-based 2FA provides the strongest security because your private key never leaves your device. However, it requires familiarity with PGP software and is less convenient for frequent logins. TOTP authenticator apps offer a good balance of security and convenience for most users. Hardware security keys provide excellent security with high convenience. Choose based on your threat model and technical comfort level.
How does Torzon protect against DDoS attacks?
Torzon uses a distributed server architecture with multiple .onion addresses and built-in DDoS protection. The platform can absorb significant attack traffic while maintaining availability through redundant infrastructure. If one mirror becomes unavailable due to attack, users can access the platform through alternative mirrors listed on our mirrors page.
Security Education Videos
Understand the cryptographic principles that protect Torzon users.
End-to-End Encryption Explained
AES Encryption - Computerphile
Quantum Computing vs Cryptography
Experience Torzon's Security Firsthand
Ready to trade on the most secure darknet marketplace? Get verified links and start your journey with confidence.